The economy has seen better days, and experts expect it to get worse before it gets better. Organizations are understandably trying to accomplish more with smaller budgets, and the best way to do that is to reduce wasteful spending. When it comes to cybersecurity budgets, the biggest challenge associated with their optimization is the critical need to maintain a strong cybersecurity posture. A single wrong decision can have far-reaching consequences, and the cost of a data breach has never been higher.
To help you optimize spending without making your organization more vulnerable to cybersecurity threats, we’ve decided to describe three common ways you may be wasting your cybersecurity budget.
Three Common Ways You May Be Wasting Your Cybersecurity Budget:
1. You Have Too Many Tools
Giving a soldier a bunch of extra weapons won’t make them any more capable of repelling an enemy attack if they don’t know how to use them correctly. Likewise, an organization doesn’t become more resistant to cyber attacks just by layering security protections on top of each other year after year.
In fact, an overabundance of tools is a far more common obstacle in threat detection and remediation than a lack of effective tools for remediating cybersecurity threats, as revealed by a survey conducted at the June 2022 RSA Conference.
Why is it such a problem to have too many security tools?
Because they may generate an overwhelming number of confusing alerts, compromising the ability of cybersecurity professionals to identify alerts that do matter and respond to them. Fortunately, the solution is simple: get rid of the tools you don’t need.
While you’re at it, you should also review your existing licenses and vendor agreements. The IT landscape is constantly evolving, so it’s possible that better options are now available. Your own IT needs may be different as well. So, stop wasting your cybersecurity budget by paying for something you don’t need anymore.
2. You Don’t Focus on the Right Threats
All organizations can encounter the same cybersecurity threats, but the likelihood of encountering them depends on a variety of factors, including the size of the organization and its industry.
For example, a large SaaS company is far more likely to be hit by a Distributed Denial of Service (DDoS) attack than a small local business with a limited online presence. Such a business will far more likely encounter a phishing or ransomware attack.
To determine which threats you should focus on, we recommend you conduct a cybersecurity risk assessment to identify, assess, and prioritize risks to your information and information systems.
The outcome of your cybersecurity risk assessment should be a list of risks and their potential impact on your organization. By also considering their likelihood, it’s possible to determine their priority using a risk matrix like the one shown below.
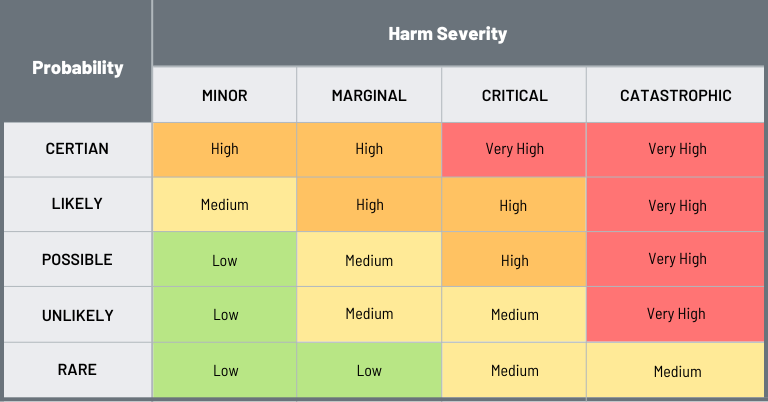
Any risk that has a fairly high probability of occurring and the potential to cause a lot of harm should be prioritized and addressed before risks that are unlikely to occur or cause a lot of harm or both.
A good example of a high-priority risk is poor password hygiene, which plays a role in 80 percent of data breaches. Similarly, unpatched vulnerabilities are responsible for one in three incidents, so it’s crucial for all systems, applications, and devices to be fully updated.
3. You Don’t Outsource Your Cybersecurity Operations
Most small and medium-sized organizations that don’t outsource at least some of their cybersecurity operations to a managed security services provider (MSSP) are wasting money. Why? Because they’re not taking advantage of the greater economies of scale from which all MSSPs benefit. They can help you get the most out of your cybersecurity budget!
Because MSSPs get volume discounts, they can provide cybersecurity capabilities, such as monitoring and cloud backup, at much lower prices than what their customers would be able to get if they were to acquire them on their own.
Whereas most smaller organizations are happy to have at least one somewhat cybersecurity-savvy employee on board, the average MSSP employs an entire team of experienced cybersecurity professionals with many different specialties. Having all this expertise concentrated under one roof allows MSSPs to quickly and accurately address cybersecurity alerts before they grow into major problems.
Conclusion: Let Us Help Make the Absolute Most Out of Your Cybersecurity Budget!
In the last few years, many organizations have increased their cybersecurity budgets to address their growing exposure to cyber attacks. In the current economic climate, many of the same organizations are looking for opportunities to reduce their expenses without also reducing their security.
If you’re among them, then the three methods described in this article may just be what you need to make the absolute most out of your cybersecurity budget.
For more information about them, contact us today.

